NPTEL Cyber Security and Privacy Week 7 Assignment Solutions

NPTEL Cyber Security and Privacy Week 7 Assignment Answer 2023
1. Which VPN technology uses leased circuits from a service provider and conducts packet switching over these leased circuits?
- Secure VPN
- Hybrid VPN
- Trusted VPN
- Transport VPN
Answer :-For Answer Click Here
2. The biometric technology criteria that describe the number of legitimate users who are denied access because of a failure in the biometric device in known as
- False reject rate
- False accept rate
- Crossover error rate
- Accountability rate
Answer :- For Answer Click Here
3. True or False: All traffic exiting from the trusted network should be filtered.
- True
- False
Answer :- For Answer Click Here
4. What term is used to describe decoy systems designed to lure potential attackers away from critical systems?
- Trap
- Honeypot
- Trace
- Sniffer
Answer :- For Answer Click Here
5. True or False: Signature-based IDPS technology is widely used because many attacks have clear and distinct signatures.
- True
- False
Answer :- For Answer Click Here
6. The method by which systems determine whether and how to admit a user into a trusted area of the organization is known as
- Attribute
- Accountability
- Access control
- Audibility
Answer :- For Answer Click Here
7. ——————denotes the rate at which fraudulent users or nonusers are allowed access to systems or areas as a result of a failure in the biometric device. This failure is also known as ————–.
- False reject rate, Type I error
- False accept rate, Type 2 error
- False accept rate, Type I error
- False reject rate, Type 2 error
Answer :- For Answer Click Here
8. Fill in the blank
——————denotes the rate at which authorised users are denied access to systems or areas as a result of a failure in the biometric device. This failure is also known as ————.
- ZChoose the correct option
- False reject rate, Type I error
- False accept rate, Type 2 error
- False accept rate, Type I error
- False reject rate, Type 2 error
Answer :- For Answer Click Here
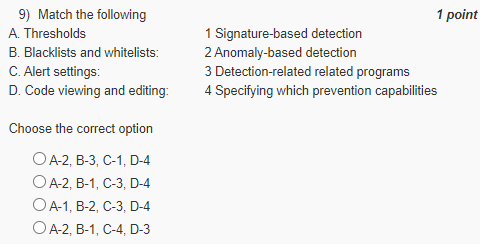
Answer :- For Answer Click Here
10. Choose the right option to fill in the blanks
(1) ————— initiates network traffic to find and evaluate service ports whereas (2) —————- uses traffic from the target network segment to evaluate the service ports available from hosts on that segment.
- 1-active vulnerability scanners, 2-passive vulnerability scanners
- 1-passive vulnerability scanners, 2-active vulnerability scanners
Answer :- For Answer Click Here
| Course Name | Cyber Security and Privacy |
| Category | NPTEL Assignment Answer |
| Home | Click Here |
| Join Us on Telegram | Click Here |





